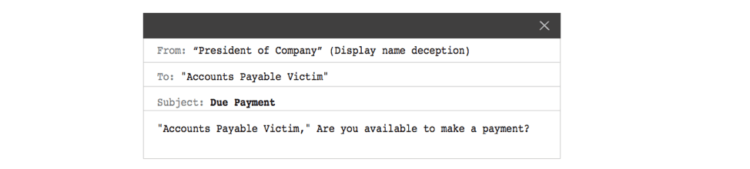
Today, Agari has published “Behind the ‘From’ Lines: Email Fraud on a Global Scale,” a historic report that I believe is the first of its kind (but definitely not the last!). During the past 10 months, Agari has captured criminal email accounts using responsible active defense techniques, granting us unparalleled access and insight into the operation of these organized crime groups. By categorizing and analyzing this data, we have been able to paint a more complete picture of these criminal organizations, their operations and trends related to email-based fraud.
Why is Agari capturing and analyzing criminal email accounts?
Today, a Nigerian cybercriminal has almost no risk of losses or getting arrested when he launches an email fraud campaign. These criminals can make a good living and even become rich, inspiring others in their communities also to make email fraud their career. Attackers are constantly changing their tactics and mix of scams based on what is working, whether to evade defenses or optimize their profits.
How can we better understand the changing tactics of cybercriminals? What if businesses and consumers could turn the tables on the attackers and jump from defense to offense? What if we could disrupt the operations of cybercriminals and make it costly to launch attacks?
It is exactly to be able to answer questions like these that Agari is developing a semi-automated system to capture and analyze cybercriminal email accounts. With the acquired insights, Agari can develop the most effective solutions to stop email fraud and abuse, make it costlier for cybercriminals to do business and provide information to law enforcement that leads to arrests and convictions. The Agari system can also act as an early warning system to prevent scams as they are being executed—by warning victims before they fall for the scam. As we learn to better protect ourselves and put more criminals behind bars, we’ll reach a tipping point where the reward of attacking people and businesses is outweighed by the risks. That is a way we can make meaningful progress towards reversing the growth of email fraud.
How does Agari capture the email accounts of these criminal organizations?
Agari uses responsible active defense techniques that involve baiting (or communicating with) criminals that launch email attacks on Agari customers. Without Agari Enterprise Protect, these email attacks would have reached the inboxes of the intended victims. With real-time access to a stream of blocked email attacks, we are able to turn attempted attacks into insights into the criminal organizations of the perpetrators. In order to avoid tipping off criminals, we don’t disclose the exact techniques we use for gaining access to attacker email accounts. However, these patent-pending techniques enable us to capture criminal email accounts in a scalable manner, and we have briefed the FBI, customers and industry organizations on the techniques and confirmed their legality.
What did Agari capture from the criminal organizations?
During the course of our research, Agari captured 78 criminal email accounts from 10 organized crime groups. And this is just the tip of the iceberg. In addition to the 78 criminal email accounts captured by Agari, we have observed communication with 188 more criminal email accounts. Our researchers were able to access a total of 59,652 messages from the inbox, sent and spam message folders of these captured criminal email accounts. These messages included communication among members within these organized crime groups, enabling our researchers to correlate their relationships. Our researchers were also able to further assign identity and location because the criminal email accounts were used for personal services, including Facebook and Uber.
How did Agari use this information to disrupt the criminal organizations?
- Agari identified three members at two of the criminal organizations, determined their locations and referred a dossier of information on the criminals to domestic and international law enforcement.
- Agari warned potential victims of several active BEC scams, where the target had yet to make wire transfers to the criminals, and helped victims who already sent money to recover funds.
- Agari referred dozens of mule accounts used by the criminal gangs to launder email fraud proceeds to financial institutions and law enforcement.
Key Email Fraud Research Findings
- 97% of people who answer a BEC email become victims
- The average BEC incident included a payment request of $35,500 (ranging from $1,500 to $201,805)
- 24% of all observed email scam attempts between 2011 and 2018 were BEC even though BEC only started in earnest in 2016
Types of Attacks Launched By The Criminal Organizations
Identity deception, such as display name deception, is at the core of all of these attacks, although the attacks take many different forms, including business email compromise (BEC), romance scams and a variety of advance fee fraud, including rental scams. There are many other types of fraud we have identified in the report, but BEC, romance scams and rental fraud are among the most common and consistent.
If we had conducted this research 10 years ago, I suspect we would have seen a much higher incidence of “Nigerian Prince” 419 scams, which was almost entirely absent in the current attacks, in spite of the fact that nine out of 10 organized crime groups we captured operate out of Nigeria. In terms of recent trends, romance scams and rental fraud have appeared consistently over the past five or so years. BEC is a more recent trend – it has really only emerged in earnest during the past two years – and yet, it already is the most common attack observed for the captured criminal accounts.
Despite the fact that BEC is the most recent trend to emerge, it is already the most popular type of email fraud; one-in-four of the attacks we detected were business email compromise. Additionally, BEC is the most successful type of email fraud, convincing 0.37 victims per 100 messages sent. This success rate increases to a staggering 3.97 victims per 100 messages sent if targets reply to an initial message (a “probe”) asking something like “Are you at your desk?”. This first probe is typically followed by “Can you help me make a payment?” as soon as the intended victim responds.
We have seen that these organized crime groups are starting to automate and script the process of sending these initial probes to their targets. It is for this reason that I believe responsible active defense techniques are so important: as criminals automate their efforts, we are faced with a threat that may become overwhelming, unless fought fiercely. For the same reason, we, too, must automate our responses to these attacks. We must cause greater friction to these criminal organizations so that they are disincentivized from attacking.