
Top 5 Challenges in Banking and How Financial Organizations Can Overcome Them
by John Walsh The banking industry is undergoing a radical shift; a shift being driven
KNOW MORE ABOUT
Security

by John Walsh The banking industry is undergoing a radical shift; a shift being driven

Even though password security is a top priority for organizations, only 55 percent of users

Ransomware. The word strikes fear into the hearts of hospital administrators, local government officers, and

Data loss of some magnitude is almost a certainty in any enterprise. The loss can
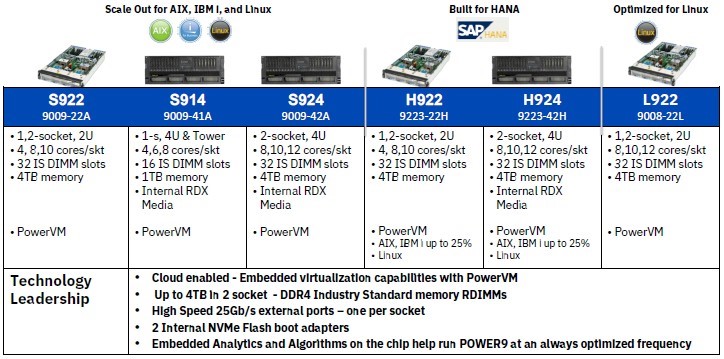
IBM recently began shipping its next-generation Power Systems servers incorporating its newly-designed POWER9 processor. These
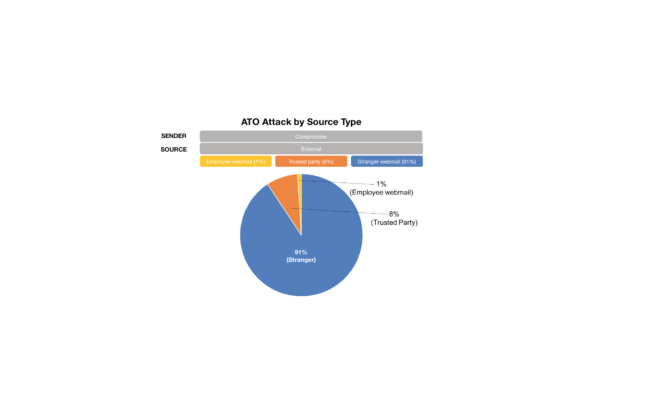
If the term “Account Takeover” (ATO) wasn’t part of your cybersecurity vocabulary before, it likely

A mind-boggling number of applications reside in the cloud without any protection. No web app

Individuals and organizations encounter new threats every day, from massive malicious spam campaigns to phishing,

Breaking-down-the-security-immune-system-proactive-database-protection-through-siem-integration. Protecting data requires strong integration of security controls. For example, a database firewall that

On Tuesday, July 25th 2017 between 9am and 3pm, IBM security experts and ActivEdge Technologies